Required RDBMS rights for packaging a database using the legacy CAST Delivery Manager Tool
Introduction
The CAST Delivery Manager Tool provides the means for Delivery Managers to configure a connection to a live Oracle Server/Microsoft SQL Server/Sybase ASE and then use this connection to perform an extraction of the relevant schemas to file using CAST’s own SQL extractor. Delivery Managers must ensure that they configure their package with a user that has sufficient rights to perform an extraction, otherwise essential data may not be included. This page provides the required rights for all RDBMS systems supported by CAST for live extraction.
Oracle Server
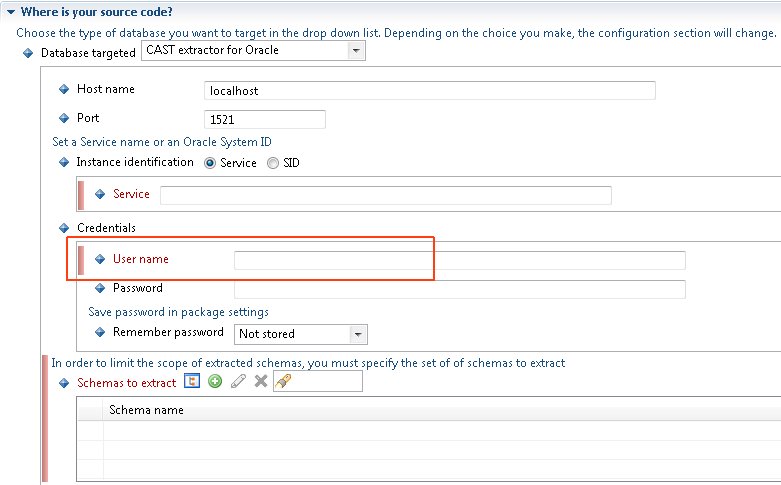
In order to carry out an extraction of the required schemas, the person in charge of the extraction (Delivery Manager or DBA) must use one of the following Oracle users:
| User | Notes |
|---|---|
| Extraction user | CAST highly recommends using a dedicated extraction user with specific privileges in order to access the required data for extraction. When using this dedicated extraction user, CAST will query the DBA_* views to access the required data - these views give access to ALL objects. Please also read the section below entitled "Note about the DBA_ARGUMENTS view and the dedicated extraction user". To create the dedicated extraction user, please run the following script as the SYS user - it will create the dedicated user and then grant the required privileges to the user (where USER_FOR_EXTRACTION is the dedicated extraction user): Note about the DBA_USERS view and the dedicated extraction userSituation
Action
Impacts
Note about DBA_MVIEW_COMMENTS / ALL_MVIEW_COMMENTS views and Oracle 9.xThe views DBA_MVIEW_COMMENTS / ALL_MVIEW_COMMENTS do not exist on Oracle 9.x, therefore when running an extraction on Oracle 9.x in whatever mode (extraction user/SYSTEM/other Oracle user), the extractor will use DBA_TAB_COMMENTS to extract comments on materialized views instead. Results are not impacted. This will typically be displayed in the log as follows: Note about the DBA_ARGUMENTS view and the dedicated extraction userSituation
ImpactsThe extraction will succeed, but:
Note that there is no impact on the source code for unwrapped
function/procedures because this code is not generated and is instead
extracted as is.
OptionsTwo options exist if you find yourself in this situation:
|
| SYSTEM | When it is not possible to use the dedicated extraction user, CAST recommends using the SYSTEM user instead. CAST will query the DBA_* views to access the required data. These views give access to ALL objects. |
| Other Oracle users | When it is not possible to use the dedicated extraction user or the SYSTEM user as outlined above, it is possible to use any other user (i.e. non-DBA user) to run your extraction - for example: the schema owner user. However, there are several drawbacks to doing this and CAST therefore does not recommend using this type of user:
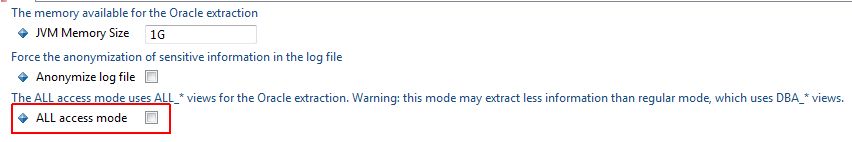
Note also that in order for the ALL_* views to be queried, the ALL access mode option must be explicitly selected in the CAST Delivery Manager Tool:
This option (when selected) explicitly allows the CAST Delivery Manager Tool to query the ALL_* views to access the required data - these views only give access to objects that the user is entitled to access. This means that CAST cannot guarantee that the extraction will contain all the required data. In addition, performance of the extraction will be reduced. By default this option is not selected, which automatically prevents the CAST Delivery Manager Tool from using the ALL_* views to access the required data. In other words, if the user name that you have entered into the "User Name" field above does not have sufficient rights to query the DBA_* views then the CAST Delivery Manager Tool will attempt to query the ALL_* views and if the ALL access mode option is not selected, then the extraction will fail.
Please avoid using the SYS user to perform extractions. Results cannot
be guaranteed.
|
Microsoft SQL Server
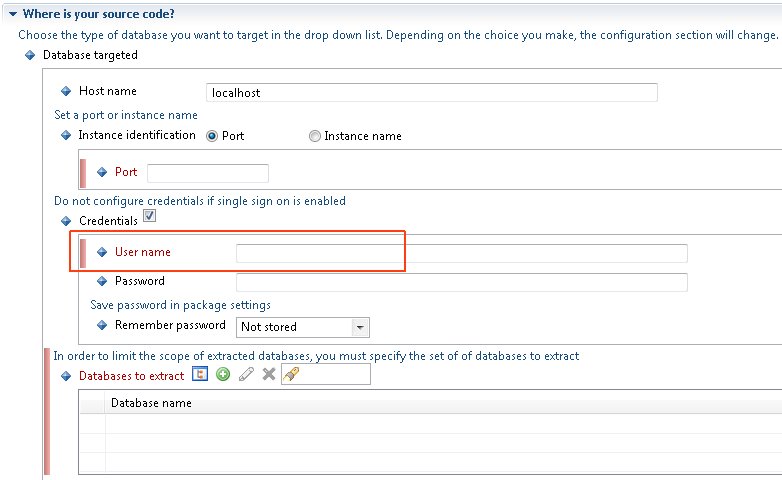
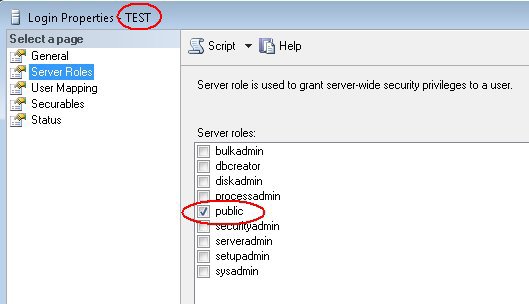
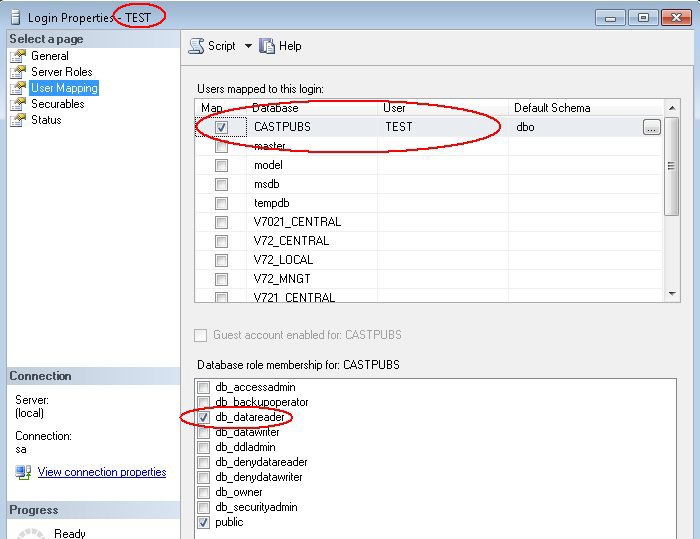
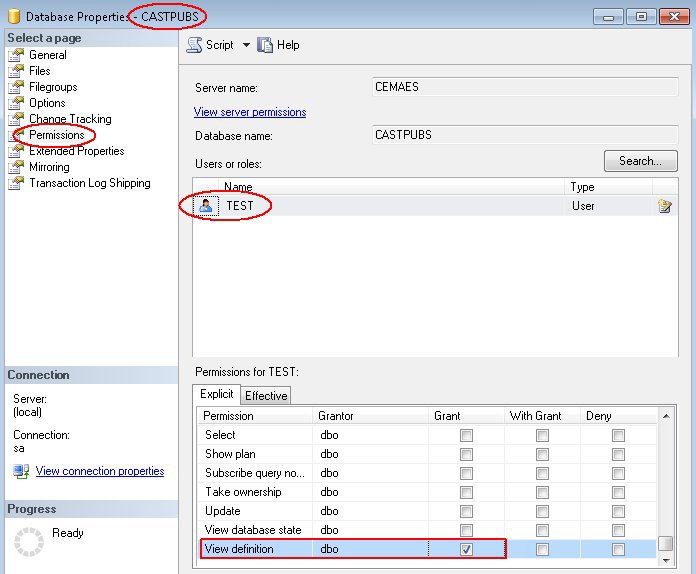
In order to carry out an extraction of the required databases, the person in charge of the extraction (Delivery Manager or DBA) must use a Microsoft SQL Server login (whether using Windows or SQL authentication) that has the following roles and permissions:
| User | Required roles and permissions |
|---|---|
| Any user with the following permissions
and roles |
An example script to assign the required role and permissions is shown below: The following screenshots show the same changes performed in the Microsoft SQL Server GUI:
|
| Extraction user | When it is not possible to grant a user the "public" Server Role and the "db-datareader" Database Role as outlined above, CAST recommends using a dedicated extraction user with specific privileges in order to access the required data for extraction. An example script to assign the required role and permissions is shown below: |
Sybase ASE
In order to carry out an extraction of the required databases, the person in charge of the extraction (Delivery Manager or DBA) must use a Sybase ASE login that has the following roles and permissions:
- CONNECT role
- SELECT permission on the following tables:
- master.dbo.sysdatabases
- master.dbo.spt_values
- master.dbo.syscurconfigs
- For each target database you want to extract, the SELECT
permission is required on the following tables:
- [%SQLdatabase%].dbo.sysusers
- [%SQLdatabase%].dbo.sysconstraints
- [%SQLdatabase%].dbo.sysreferences
- [%SQLdatabase%].dbo.sysobjects
- [%SQLdatabase%].dbo.syscolumns
- [%SQLdatabase%].dbo.sysindexes
- [%SQLdatabase%].dbo.syscomments
- [%SQLdatabase%].dbo.systypes